How SPF, DKIM, and DMARC Improve Email Deliverability
SPF, DKIM, and DMARC are essential for improving email deliverability and protecting your domain from email spoofing and phishing. These protocols work together to authenticate your emails, secure your domain, and ensure messages reach inboxes instead of spam folders. Here's a quick breakdown:
- SPF (Sender Policy Framework): Verifies if the sending server is authorized by your domain.
- DKIM (DomainKeys Identified Mail): Adds a digital signature to confirm email content isn't altered during transit.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): Aligns SPF and DKIM, enforces policies, and provides reports on domain misuse.
Without these protocols, your emails risk being flagged as spam, blocked, or exploited by attackers. Setting them up involves configuring DNS records for SPF, generating DKIM keys, and creating DMARC policies. Tools like Infraforge simplify this process by automating configurations and improving email management.
Key Takeaways:
- Proper setup of SPF, DKIM, and DMARC boosts sender reputation and inbox placement.
- DMARC reports help monitor and refine email authentication.
- Automated tools reduce errors and save time when managing multiple domains.
These protocols aren't optional - they're critical for secure, reliable email communication.
How SPF, DKIM, and DMARC Work
How SPF (Sender Policy Framework) Works
Think of SPF as a guest list for your domain’s email servers. By setting up SPF, you define which servers are allowed to send emails on behalf of your domain.
It starts with creating an SPF record in your domain's DNS settings. This record lists the IP addresses and servers you’ve authorized to send emails. When someone receives an email from your domain, their email server checks this SPF record. It looks at the email’s "envelope from" address (not the visible "From" field) and queries the DNS for your domain’s SPF record. If the sending server’s IP matches one of the authorized IPs, the email passes SPF authentication. If it doesn’t match, the email fails.
The "-all" directive in the SPF record is crucial - it tells receiving servers to reject any emails that don’t come from your authorized list. If you prefer a less strict approach, you can use "~all", which flags unauthorized emails as suspicious but doesn’t immediately reject them.
Next, DKIM ensures that your email’s content hasn’t been tampered with.
How DKIM (DomainKeys Identified Mail) Works
DKIM focuses on verifying that the content of an email remains unchanged during transit. While SPF checks the sender's server, DKIM ensures the integrity of the email itself.
The process starts with generating two cryptographic keys: a private key, which stays secure on your email server, and a public key, published in your DNS records. When your server sends an email, it uses the private key to create a unique digital signature based on parts of the email, like its headers and body.
This signature is added to the email in the DKIM-Signature header. When the recipient's server gets the email, it retrieves your public key from DNS and uses it to verify the signature. If everything matches, it confirms two things: the email genuinely came from your domain, and the content hasn’t been altered.
DKIM uses a selector (a label included in the signature) to tell the receiving server which public key to use for verification. For example, you might have one selector for your regular emails and another for emails sent through a marketing platform.
Because the signature covers specific elements of the email, even tiny changes - like altering a single word - will cause the verification to fail. This makes it incredibly hard for attackers to tamper with emails undetected.
DMARC ties everything together by coordinating SPF and DKIM and enforcing policies.
How DMARC (Domain-based Message Authentication, Reporting, and Conformance) Works
DMARC acts as the orchestrator, combining the strengths of SPF and DKIM while adding its own layer of protection. It ensures alignment between the authenticated domain and the visible "From" header - the one recipients actually see.
The key idea behind DMARC is alignment. For an email to pass DMARC, it must pass either SPF or DKIM authentication, and the authenticated domain must match (or align with) the domain in the "From" header. There are two types of alignment: relaxed (where subdomains, like mail.example.com, can align with example.com) and strict (requiring an exact domain match). Many organizations start with relaxed alignment and tighten it over time.
DMARC policies come in three options: "none", which monitors emails without enforcement; "quarantine", which sends suspicious emails to spam folders; and "reject", which blocks them outright. Most start with "none" to collect data and gradually move to stricter policies after addressing legitimate email sources that fail authentication.
One standout feature of DMARC is its reporting capability. It provides two types of reports:
- Aggregate reports, which summarize authentication results and patterns.
- Forensic reports, which offer detailed insights into specific email failures.
These reports help you identify who’s sending emails on your behalf and spot potential security risks.
DMARC also includes a percentage tag (pct=) that allows you to test policies on a fraction of your email traffic. For instance, setting pct=25 applies the policy to 25% of your emails, letting you fine-tune the setup before rolling it out fully. Gradually increasing this percentage ensures a smooth transition to stricter enforcement.
How These 3 Protocols Work Together
The Combined Workflow of SPF, DKIM, and DMARC
When an email is received, the recipient's server doesn’t rely on a single protocol to verify its authenticity. Instead, it checks SPF, DKIM, and DMARC in sequence to ensure the email is legitimate. These protocols work together, each playing a distinct role in protecting against email spoofing and fraud.
The process starts with SPF verification, where the server checks if the sending IP address is authorized in the domain’s SPF record. At the same time, it performs DKIM validation by using the public key from DNS to confirm the email’s digital signature. Importantly, SPF and DKIM are verified independently, meaning an email can pass one and fail the other.
This is where DMARC steps in. DMARC doesn’t just check if SPF or DKIM passed - it looks for alignment. The domain authenticated by SPF or DKIM must match the domain in the visible "From" header. This alignment ensures attackers can’t exploit legitimate SPF or DKIM records while spoofing the "From" address to trick recipients.
For an email to pass DMARC, at least one protocol (SPF or DKIM) must succeed and align with the "From" domain. For instance, if SPF fails but DKIM passes with proper alignment, the email still clears DMARC. This redundancy is intentional, offering a safety net when one protocol fails - such as when email forwarding disrupts SPF alignment.
Finally, the recipient’s server applies the DMARC policy. If the policy is set to p=none, the server logs the authentication results but delivers the email regardless. With p=quarantine, emails that fail DMARC are sent to spam. A p=reject policy blocks the email entirely. The pct= tag allows gradual implementation by applying the policy to only a portion of emails during testing. This layered process ensures that even if one protocol encounters issues, the others maintain email security.
Common Setup Mistakes and Their Impact
Even small missteps in configuring these protocols can disrupt email delivery and damage trust. A common mistake is deploying DMARC too aggressively. Jumping straight to p=reject without adequate testing can result in legitimate emails being blocked, frustrating customers and partners.
SPF misconfigurations are frequent when businesses use multiple email services. If your SPF record doesn’t include all authorized sending servers, those emails will fail authentication and likely be marked as spam.
DKIM issues can also cause headaches. For example, if DKIM keys expire, all emails will fail validation until the DNS records are updated. Similarly, content changes after signing - like a forwarding service adding disclaimers - can break the DKIM signature, leading to errors such as "DKIM body hash not verified".
DMARC alignment problems add another layer of complexity. Strict alignment settings (aspf=s or adkim=s) can cause legitimate emails to fail, especially when they’re forwarded through services that modify headers. If neither SPF nor DKIM passes and aligns, the recipient’s mail server will take action based on the DMARC policy, which could mean blocking or filtering the message.
These errors don’t just affect individual emails - they can harm your sender reputation over time. High bounce rates, spam complaints, and blocklisted IP addresses can lead to a downward spiral that’s tough to reverse.
Benefits for Cold Email Outreach
For cold email campaigns, getting these protocols right is non-negotiable. Cold emails are already scrutinized more closely by spam filters, so even minor authentication failures can drastically reduce your chances of landing in the inbox.
Using SPF, DKIM, and DMARC together provides multiple layers of verification that signal trust to receiving servers. Major email providers like Gmail, Outlook, and Yahoo rely heavily on these authentication results when deciding whether to flag an email as spam. Emails that pass all three protocols are far more likely to appear in recipients’ primary inboxes.
Another critical factor is brand protection. DMARC helps prevent phishing attacks by ensuring that only authenticated emails can use your domain. This safeguards your reputation, making prospects more likely to trust and engage with your emails.
For businesses running large-scale outreach, managing these protocols becomes even more critical. Advanced platforms like Infraforge simplify this process by automating the configuration of SPF, DKIM, and DMARC across multiple domains and IPs. By automating these tasks, such platforms eliminate common errors and ensure consistent authentication, helping you maintain high deliverability as your campaigns grow.
Step-by-Step Setup Guide for SPF, DKIM, and DMARC
Now that you understand the basics, it’s time to implement SPF, DKIM, and DMARC to protect your emails. Each protocol plays a specific role in securing your domain, and the setup process requires careful attention to DNS records. Let’s break it down step by step.
Setting Up SPF Records
SPF records let receiving servers know which IP addresses are authorized to send emails on your domain’s behalf. To get started, list all services you use to send emails, such as your email provider, marketing tools, and any third-party apps.
You’ll create an SPF record as a TXT entry in your DNS settings. The format begins with v=spf1, followed by mechanisms that define authorized senders. For instance, if you use Google Workspace and Mailchimp, your record might look like this:
v=spf1 include:_spf.google.com include:servers.mcsv.net ~all.
include:references other domains’ SPF records.ip4:andip6:specify individual IP addresses.- Use
~allfor a soft fail or-allfor a hard fail.
Keep your SPF record under 255 characters and ensure it doesn’t exceed 10 DNS lookups. Each include: counts as one lookup, and going over the limit can cause SPF to fail. If you’re running out of space, consider consolidating your email services or using an SPF flattening tool.
Before finalizing, test your SPF record using tools like MXToolbox or dig commands. Even a small typo can disrupt email authentication. Once verified, you’re ready to move on to DKIM.
Setting Up DKIM Keys
DKIM secures your emails by adding a digital signature, which is verified using cryptographic keys. To set it up, generate a key pair, publish the public key in your DNS, and configure your server to sign outgoing messages.
Most email providers simplify DKIM setup. For example, Google Workspace can generate the necessary DNS record for you. You’ll receive a TXT record with a name like selector._domainkey.yourdomain.com. The “selector” identifies which key to use - common examples include "default", "google", or custom labels like "2024-jan." The record value contains the public key and other details.
For better security, rotate your DKIM keys every 6–12 months. When switching keys, add the new key to your DNS first, update your email server, and wait a few days before removing the old key. This ensures emails in transit can still be verified.
If you use multiple email services, each will require its own DKIM selector and key pair. For example, your primary email, marketing platform, and transactional email service might each have separate DKIM records.
With DKIM in place, the next step is configuring DMARC to tie everything together.
Setting Up DMARC Policies
DMARC works by combining SPF and DKIM while giving you control over how authentication failures are handled. Start with a monitoring policy to understand your email flow before enforcing stricter rules.
Create a DMARC TXT record at _dmarc.yourdomain.com. A basic record might look like this:
v=DMARC1; p=none; rua=mailto:dmarc@yourdomain.com; ruf=mailto:dmarc-forensic@yourdomain.com; pct=100.
p=none: Monitors failed emails without taking action.rua: Specifies where to send aggregate reports.ruf: Designates the address for detailed forensic reports.
This monitoring phase helps you spot legitimate email sources that aren’t authenticated yet. Once you’ve reviewed the reports, gradually tighten your policy - move from p=none to p=quarantine, and eventually to p=reject. Use the pct tag to test policies on a portion of your emails, such as pct=25 for 25% of your email traffic.
Set alignment rules with aspf for SPF and adkim for DKIM. Relaxed alignment (aspf=r and adkim=r) allows subdomains to pass, while strict alignment (aspf=s and adkim=s) requires exact matches. Start with relaxed alignment to avoid blocking legitimate emails from subdomains or forwarding services.
Regularly monitor your DMARC reports using tools like Postmark’s DMARC analyzer or dmarcian. These reports highlight which IP addresses are sending emails from your domain and whether they pass authentication. Watch for unexpected sources, as they could indicate spoofing or forgotten services that need to be added to your SPF record.
For cold email campaigns, a p=reject policy signals strong domain security to receiving servers, which can improve your deliverability. However, double-check that all your tools and IPs are properly authenticated before enforcing strict policies.
"Infraforge quickly helped to solve a challenge regarding email deliverability. What I like about Infraforge is its ease of use and quality of support." - Silver L, CEO
Platforms like Infraforge simplify this entire process by automating DNS setup and maintenance. For example, Infraforge configures DKIM, SPF, and DMARC records for every domain added to its platform, ensuring everything is set up correctly while reducing the risk of errors.
Infraforge vs Other Email Infrastructure Solutions
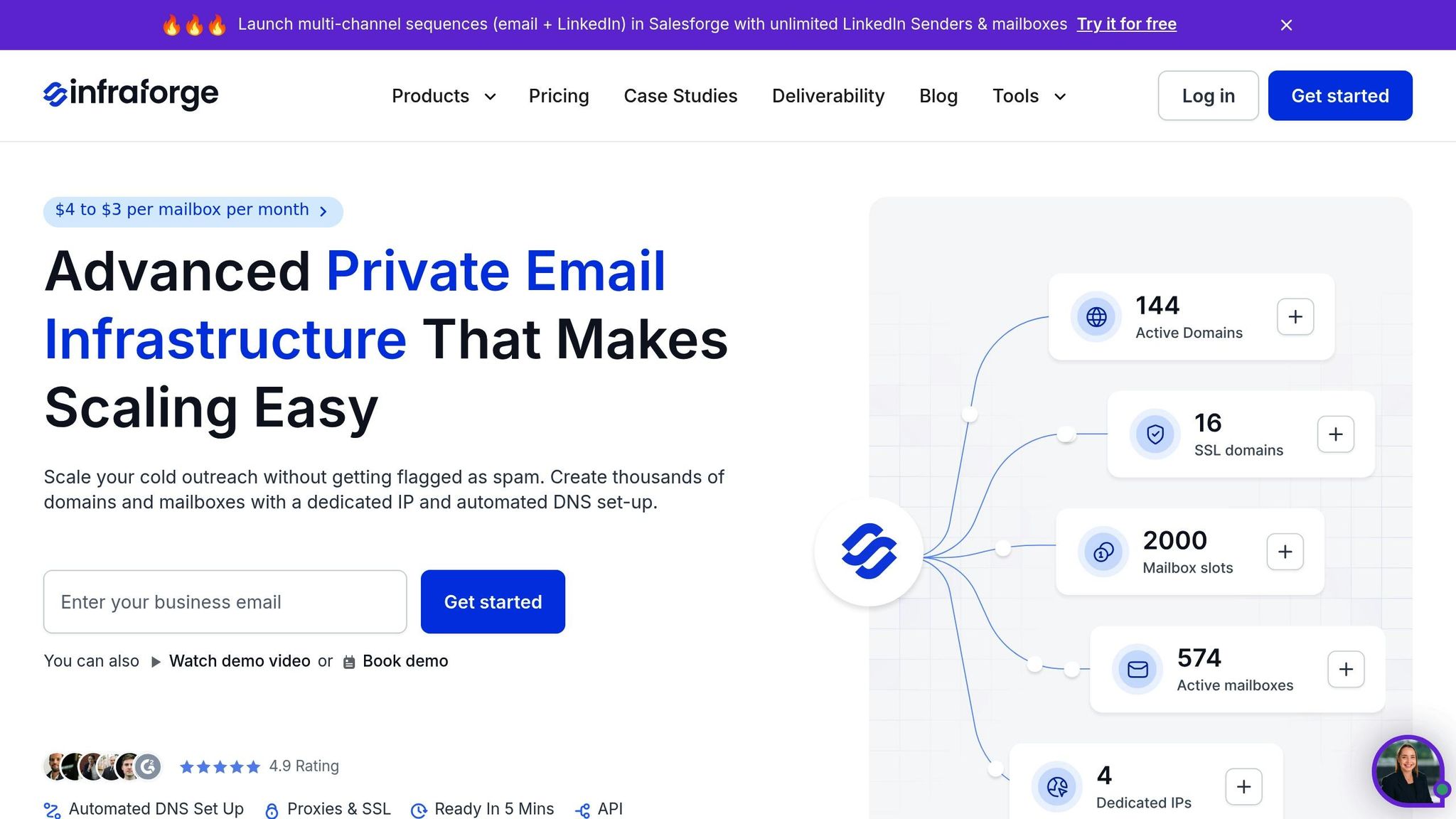
Once your authentication protocols are in place, it's worth examining how Infraforge simplifies email management compared to traditional solutions. While conventional email providers often require time-consuming manual DNS configuration, Infraforge automates the setup for SPF, DKIM, and DMARC, removing much of the hassle.
Infraforge Features
Infraforge takes the complexity out of email setup by automating processes that could otherwise take hours. It handles SPF, DKIM, and DMARC configurations automatically for every domain you add. This automation builds on the authentication foundations previously discussed.
The setup process is straightforward: you simply update your domain nameservers to Infraforge's DNS editor, and the platform takes care of the rest. Your first domain and mailbox can be fully operational within 5 minutes, a stark contrast to the hours required for manual configurations.
Infraforge goes beyond basic authentication. It offers dedicated IP addresses to improve sender reputation, pre-warmed domains and mailboxes to build trust with receiving servers, and SSL and domain masking for better security. Additionally, the platform supports bulk DNS updates, making it easy to update multiple domains' DNS records in just a few clicks.
For businesses looking to scale, Infraforge provides an API for programmatic management and integrates seamlessly with tools like Salesforge. Its Masterbox feature offers a centralized view of all emails across accounts, simplifying the monitoring of deliverability and engagement across multiple campaigns.
Infraforge vs Competitors
When compared to both traditional email providers and other infrastructure solutions, Infraforge offers several distinct advantages:
| Feature | Infraforge | Google Workspace | Microsoft 365 | SendGrid | Mailgun |
|---|---|---|---|---|---|
| Automated DNS Setup | Complete automation | Manual configuration | Manual configuration | Manual configuration | Manual configuration |
| Pre-warmed Mailboxes | Provided | Not available | Not available | Not available | Not available |
| Dedicated IPs | Available with multi-IP provisioning | Shared IPs only | Shared IPs only | Available (paid add-on) | Available (paid add-on) |
| Cold Email Focus | Purpose-built | General business email | General business email | Transactional focus | Transactional focus |
| Cost (200 mailboxes) | $651/month | $1,680/month | $1,200/month | Variable | Variable |
Infraforge stands out with its cost-effectiveness. Managing 200 mailboxes costs $651 per month with Infraforge, compared to $1,680 per month for Google Workspace and $1,200 per month for Microsoft 365. This translates to savings of up to 61%, while still offering specialized features that general email providers lack.
Unlike Google Workspace or Microsoft 365, which are designed for general business communication, Infraforge is tailored for cold email outreach. Every feature - from automated technical setup to built-in deliverability tools - is designed to support high-volume, high-deliverability campaigns. These differences underscore why Infraforge is a standout choice for cold email outreach.
Why Choose Infraforge
Infraforge's automation removes the technical hurdles that often complicate email authentication projects. When scaling operations or adding new domains, the bulk DNS update feature allows you to manage multiple domains simultaneously. Traditional providers, in contrast, require manual setup for each new domain, increasing the likelihood of errors.
The platform's integration with Salesforge completes its ecosystem, making it an efficient solution for cold outreach. With Infraforge, you can focus on crafting effective campaigns rather than getting bogged down by technical configurations.
"Infraforge quickly helped to solve a challenge regarding email deliverability. What I like about Infraforge is its ease of use and quality of support." - Silver L, CEO
Conclusion: Using SPF, DKIM, and DMARC for Better Deliverability
SPF, DKIM, and DMARC are at the heart of modern email security and play a vital role in ensuring your emails reach their intended recipients. Together, they confirm your identity as a trusted sender and reduce the chances of your messages being marked as spam.
When set up correctly, these protocols can significantly improve your email campaigns. They help increase deliverability, protect your brand from being impersonated, and maintain customer trust by keeping phishing attempts at bay.
DMARC stands out by offering clear policies for handling emails that fail SPF or DKIM checks. It also provides detailed reporting that helps you monitor and refine your email authentication efforts. However, manually managing these protocols, especially across multiple domains, can be a tedious and error-prone process.
That’s where automation tools like Infraforge come in. By automating the setup of SPF, DKIM, and DMARC for every new domain and offering features like bulk DNS updates, Infraforge streamlines the process. This eliminates the headaches of manual configuration and ensures your email authentication stays robust as your business grows - all with ongoing support included in your subscription.
For businesses aiming to secure their email operations and improve deliverability, these protocols are non-negotiable. The key lies in implementing them efficiently while keeping scalability in mind.
FAQs
How do SPF, DKIM, and DMARC improve email deliverability and prevent spoofing?
SPF, DKIM, and DMARC work hand-in-hand to safeguard your emails from spoofing and improve their chances of landing in inboxes rather than spam folders. Here's how they work:
- SPF (Sender Policy Framework): This checks if an email is sent from an authorized server listed in your domain's DNS records.
- DKIM (DomainKeys Identified Mail): Adds a digital signature to your emails, ensuring they haven't been tampered with during transit.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance): Aligns SPF and DKIM results with your domain's policies, helping email servers decide how to handle unauthorized messages.
By using these protocols, you can minimize phishing attempts, build trust with your audience, and boost your sender reputation - all of which lead to better email deliverability. For businesses running large-scale email campaigns, tools like Infraforge make this process easier. They offer features like automated DNS setup, pre-warmed domains, and dedicated IPs to ensure your emails perform reliably every time.
What mistakes should I avoid when setting up SPF, DKIM, and DMARC for my domain?
When configuring SPF, DKIM, and DMARC, certain mistakes can cause email authentication problems and hurt deliverability. For SPF, common issues include incorrect syntax, forgetting to list all authorized senders, or surpassing the 10 DNS lookup limit. With DKIM, problems arise from using weak encryption keys, not rotating keys periodically, or misconfiguring DNS records. As for DMARC, skipping the policy setup or failing to ensure SPF and DKIM align with the 'From' domain are frequent missteps.
To steer clear of these problems, double-check that all DNS records are accurate, account for all legitimate email sources, and periodically review your configurations. Properly implementing these protocols not only boosts email deliverability but also helps shield your domain from spoofing and phishing attacks.
How does Infraforge make it easier to manage SPF, DKIM, and DMARC for multiple domains?
Infraforge takes the hassle out of managing SPF, DKIM, and DMARC by automating the setup and configuration of these critical email authentication protocols. This streamlines domain authentication, minimizes errors, and boosts email deliverability.
By offering automated DNS setup and continuous monitoring, Infraforge not only saves you valuable time but also ensures uniformity across all your domains. It helps eliminate misconfigurations that might cause your emails to end up in spam folders, making it a smart choice for handling large-scale email campaigns with ease.